Rio Grande do Norte
How to Automatically Repeat Loop YouTube Videos Artictle
Configuration pages are now easier to read, easier to understand, and work better on a wide range of screens. See the Jenkins issue tracker for a list of plugins known to have issues with the change. Always enable the agent-to-controller security subsystem. Remove the admin-customizable allowlists for callables and file paths. Remove the ability to access some files on the controller from agents. Use the Plugin Manager to upgrade incompatible plugins.
- Using ListenOnRepeat, paste the video’s URL into the search box and press Enter.
- Watch your favorite YouTube video over and over again without pressing replay.
- The platform lets you stream movies online with no lags at all, so you can enjoy watching what you love.
- As of the release of Firefox 57 and Greasemonkey 4.0, a lot of users scripts no longer work.
The Apache Commons Collections library is also in widespread use beyond the Hadoop ecosystem. At this time, no specific attack vector for this vulnerability has been identified as present in Cloudera Products. When you create a security advisory for a public repository on GitHub, you have the option of providing an existing CVE identification number for the security vulnerability. If you want a CVE identification number for the security vulnerability in your project, and don’t already have one, you can request a CVE identification number from GitHub. Requesting a CVE identification number doesn’t make your security advisory public. If your security advisory is eligible for a CVE, GitHub will reserve a CVE identification number for your advisory.
Pager plugin#
VPN can be a very helpful tool for those who want more privacy online. It can be imagined as a virtual tunnel that connects your computer to the Internet via another computer. This metaphorical tunnel is much more private than your regular connection – the best feature it is impossible to track your online activity.
It became hugely popular several years ago, as a way of finding torents and magnet links that are up to date and could be downloaded conveniently in a torent download tool. However, its popularity was largely due to the fact that it made it very easy to discover links to illegal files, such as those that breach copyright laws in several countries. Other torenting sites are just as dangerous, so you might be good with pretty much any virtual private network . Interaction with malicious web content, be it direct or indirect can lead to serious data breaches.
Enabling the loop feature on a YouTube video using a mobile device
Rotate plugin support features like rotate clockwise remove Ehiz, rotate anticlockwise, flip horizontal, flip vertical with single click. String”.lg-toolbar”Specify where the autoplay controls should be appended.
Rio Grande do Norte
PENDÊNCIAS – CÂMARA DE VEREADORES GASTAM QUASE R$ 50 MIL REAIS COM CARRO QUE MAL APARECE EM SERVIÇO.

A Câmara Municipal de Pendências voltou a chamar atenção pelo uso questionável de recursos públicos. Apenas em 2025, os cofres do Legislativo bancaram R$ 35.623,45 em combustíveis e mais R$ 13.256,00 em oficina mecânica, totalizando R$ 48.879,45 com um único veículo oficial.
O carro em questão é um Volkswagen Polo, modelo que, além de antigo, já não atende às necessidades operacionais da Câmara. Mesmo assim, os gastos seguem elevados, sem que a população consiga perceber, na prática, a real utilização do veículo no dia a dia da Casa.
O valor gasto com combustível chama ainda mais atenção diante da baixa visibilidade do automóvel em atividades institucionais. Para muitos moradores, é difícil entender como um carro pouco visto em circulação consegue consumir quase R$ 40 mil em combustíveis em apenas um ano.
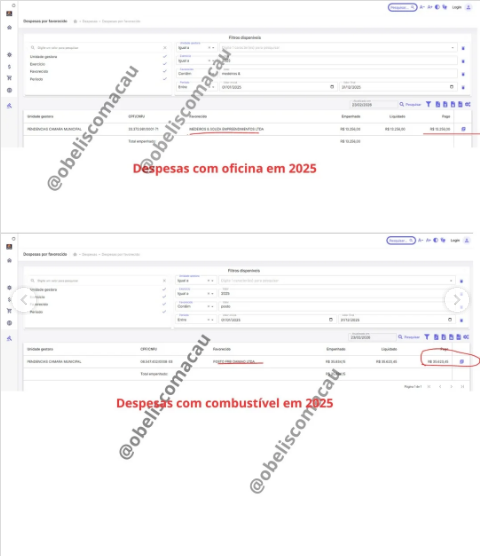
Apesar dos números expressivos, não há registro de questionamentos internos, pedidos de explicação ou ações de contenção de gastos. Mais uma vez, o corporativismo parece prevalecer, e os vereadores deixam de cumprir um de seus papéis centrais: fiscalizar o uso do dinheiro público, inclusive dentro da própria instituição.
Diante desse cenário, fica a pergunta que ecoa fora das paredes do Legislativo:
quem fiscaliza os vereadores quando eles não fiscalizam a si mesmos?
Rio Grande do Norte
GUAMARÉ VIRA CENTRO DO DESENVOLVIMENTO REGIONAL NO 6º ENCONTRO TERRITÓRIOS EMPREENDEDORES

Guamaré sedia primeiro dia do 6º Encontro Territórios Empreendedores com programação voltada à integração, planejamento e desenvolvimento regional
Guamaré (RN) foi palco, nesta quinta-feira, de um dia inteiro dedicado ao diálogo, ao aprendizado e à construção coletiva.
O Centro de Convenções do município recebeu lideranças, empresários, representantes de instituições parceiras e diversos setores do território para o primeiro dia do 6º Encontro Territórios Empreendedores, iniciativa realizada com o apoio da Prefeitura de Guamaré, da Secretaria Municipal de Turismo, da Secretaria de Indústria e Comércio, e do Programa LÍDER / Territórios Empreendedores do Sebrae-RN.
A programação teve início com a recepção e integração dos participantes, seguida da apresentação do Programa LÍDER, que orienta políticas e ações voltadas ao desenvolvimento territorial sustentável. Na sequência, novos integrantes participaram de uma roda de conversa, fortalecendo vínculos e alinhando expectativas.
Durante o dia, aconteceram ainda uma oficina de storytelling, atividades voltadas à diversidade e união e dinâmicas para construção dos eixos prioritários da região, bem como a definição dos objetivos estratégicos que irão nortear os próximos passos do território.
O encerramento foi marcado pela troca de experiências entre os participantes e pelo convite para o fórum comunitário, reforçando o caráter colaborativo e mobilizador do encontro.
Segundo a organização, o evento reafirma o potencial transformador de Guamaré e dos municípios vizinhos quando atuam de forma integrada, participativa e orientada para o futuro.
Rio Grande do Norte
Esgotamento Sanitário em Apodi beneficiará mais de 21 mil pessoas

A cidade de Apodi viveu, nesta sexta-feira (11), um momento aguardado há décadas: o início oficial das obras do sistema de esgotamento sanitário. A ordem de serviço foi assinada pela governadora Fátima Bezerra, em solenidade realizada na Câmara Municipal.
“Hoje celebramos um passo decisivo para Apodi. Estamos falando de uma obra esperada há muitos anos, que agora se torna realidade. São R$ 54 milhões garantidos com muito esforço e parceria. Através do PAC, junto ao presidente Lula, conseguimos tirar do papel essa que será uma das obras mais estruturantes para a cidade. E não estamos aqui com promessas: estamos com atitude, com compromisso. Até o final de 2026, Apodi terá 100% de cobertura de esgotamento sanitário”, afirmou a governadora Fátima Bezerra durante a cerimônia.
Com investimento inicial de quase R$ 18 milhões, a primeira etapa prevê a recuperação e instalação de redes de esgoto, a conclusão da Estação Elevatória II, a implantação de um módulo da Estação de Tratamento com capacidade para 20 litros por segundo, além de 1.500 ligações domiciliares. A obra, executada pela Construtora Cristal, vai beneficiar diretamente 21 mil moradores. A segunda etapa será iniciada após a conclusão desta fase e ampliará a cobertura para toda a cidade.
O prefeito de Apodi, Luis Sabino Costa, destacou o caráter coletivo da conquista: “Essa luta é da Câmara, do povo de Apodi, da classe política e do Executivo municipal. Tenho o maior orgulho de receber a governadora hoje para dar início a uma obra pela qual lutamos há mais de 25 anos. Começamos esse processo lá em 2009, com a elaboração do Plano Municipal de Saneamento Básico, e seguimos batalhando com a Caern e o governo estadual. É uma conquista de todos nós.”
A obra corrige falhas históricas. Segundo o diretor-presidente da Caern, Roberto Linhares, os investimentos realizados em 2007 não resultaram em um sistema funcional. “Agora, com planejamento, vamos entregar uma estrutura eficiente, moderna, que protege a saúde da população e o principal cartão-postal da cidade: a Lagoa de Apodi.”
O início da segunda etapa da obra de esgotamento será realizado após a conclusão da primeira. Ao final, Apodi contará com três Estações Elevatórias, uma Estação de Tratamento, 22 quilômetros de redes coletoras, 4,8 quilômetros de emissários e mais de 8 mil ligações domiciliares, transformando de forma definitiva a infraestrutura sanitária do município.
Além do sistema de esgotamento sanitário, o Governo do Estado tem atuado em várias frentes no município. Investiu na modernização das escolas estaduais Professor Antônio Dantas e Maria Zenilda Gama, aplicando mais de R$ 1,5 milhão em melhorias de infraestrutura. Também viabilizou, em parceria com a Universidade Agrícola da China e instituições locais, a instalação da primeira Residência Tecnológica de Mecanização da Agricultura Familiar da América Latina. Na saúde, o Hospital Regional Hélio Morais Marinho passou a oferecer cirurgias ortopédicas. E na área da segurança, o efetivo da Polícia Civil foi ampliado e o município passou a contar com um Posto Avançado do Corpo de Bombeiros desde 2023.
Além das autoridades já citadas, prestigiaram o evento o vice-prefeito de Apodi Ivanildo Lima; o presidente da Câmara Municipal de Apodi, Felipe Gustavo; o prefeito de Felipe Guerra, Salomão Gomes; os deputados estaduais Isolda Dantas e Neilton Diógenes; a vereadora de Natal, Samanda Alves, o Superintendente do BNB Jeová Lins e Aldemir Freire, diretor de Planejamento do BNB; João Hélio e Itamar Manso, representando o Sebrae-RN e Alaniel Costa, representando a construtora Cristal.
Também estavam presentes os secretários estaduais Cadu Xavier (Fazenda), Gustavo Coelho (Infraestrutura), Coronel Araújo Silva (Segurança e Defesa Social), Alan Silveira (Desenvolvimento Econômico), Ivanilson Maia (adjunto do Gabinete Civil), Osmir Monte (adjunto da Defesa Social), Werner Farkatt (Idema)
Outras personalidades locais como a professora Lusia Gomes Pinto, diretora da 13ª regional de Educação; o empresário Marcelo Bernardo, presidente da Associação Comercial e Empresarial de Apodi; o sindicalista Agnaldo Fernandes, presidente do Sindicato dos Trabalhadores Rurais (STR) de Apodi; professor Rômulo Magno Oliveira de Freitas, diretor do Instituto Federação de Educação, Ciência, Cultura e Tecnologia do Rio Grande do Norte (IFRN) em Apodi e Leylla Carla Dantas de Sena, presidente da Academia Apodiense de Letras (AAPOL) compareceram ao evento.

 Porto do Mangue2 semanas atrás
Porto do Mangue2 semanas atrásCARNAVAL DE PORTO DO MANGUE: R$ 8 MILHÕES ARRECADADOS E UMA ESTRUTURA QUE GERA POLÊMICA

 Porto do Mangue4 dias atrás
Porto do Mangue4 dias atrásMP visita Porto do Mangue e apura supostas irregularidades graves na Saúde

 Serra do Mel1 mês atrás
Serra do Mel1 mês atrásPrefeitura de Serra do Mel inicia emissão e recadastramento de carteirinhas do transporte estudantil

 Porto do Mangue2 dias atrás
Porto do Mangue2 dias atrásSem Agricultores, Faustino Surge em Evento no Assentamento Apenas com Motorista e Contratados

 Serra do Mel1 mês atrás
Serra do Mel1 mês atrásSerra do Mel chega à terceira final consecutiva do Matutão Master RN 40+

 Rio Grande do Norte6 dias atrás
Rio Grande do Norte6 dias atrásPENDÊNCIAS – CÂMARA DE VEREADORES GASTAM QUASE R$ 50 MIL REAIS COM CARRO QUE MAL APARECE EM SERVIÇO.

 Pendências6 dias atrás
Pendências6 dias atrásDRA. LAYS HELENA FAZ BALANÇO DE SUA GESTÃO EM LEITURA ANUAL NA CÂMARA MUNICIPAL DE PENDÊNCIAS.






















